Important: Be sure to write down your computer’s current network settings, so you can refer to them to reset your computer after the appliance is configured.
Windows 2000: (Record your existing network settings so you can revert back to them.)
1. Go to Start>Settings>Control Panel.
2. Double-click Network and Dial-up Connections.
3. Double-click Local Area Connection to open the Local Area Connection Status window.
4. Click Properties to open the Local Area Connection Properties window.
5. Select Internet Protocol (TCP/IP) to open the Internet Protocol (TCP/IP) Properties window.
6. Click Properties.
7. Record your existing network and DNS settings.
8. Click Obtain an IP address automatically and Obtain DNS server address automatically.
9. Click OK three times, to close the Internet Protocol (TCP/IP) Properties window, the Local Area Connection Properties window, and the Local Area Connection Status window.
10. Return to the Installation Steps section to configure the appliance’s network settings.
If you cannot configure the appliance, open an MS-DOS window and enter ipconfig /release. Then enter ipconfig /renew. The resulting IP address should be 192.168.255.254. If not, see the “Troubleshooting” section.
Windows XP: (Record your existing network settings so you can revert back to them.)
1. Go to Start>Control Panel.
2. Double click Network Connections to open the window.
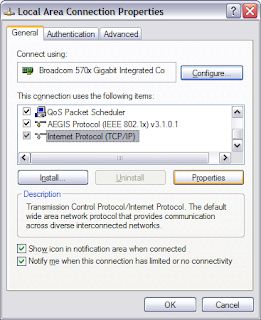
3. Select Internet Protocol (TCP/IP) and click Properties.
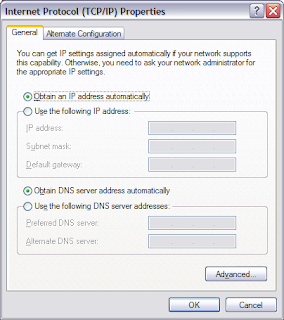
4. On the General tab, click Obtain an IP address automatically and Obtain DNS server address automatically.
5. Click OK to close the Internet Protocol (TCP/IP) Propertieswindow.
6. Click OK to close the Local Area Connection Properties window and close the Control Panel.
7. Return to the Installation Steps to configure the appliance’s network settings.