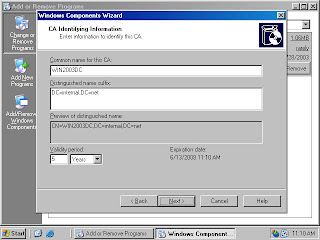
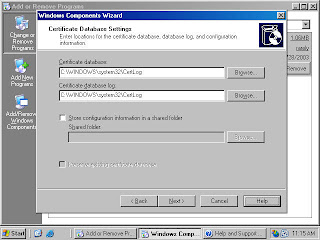
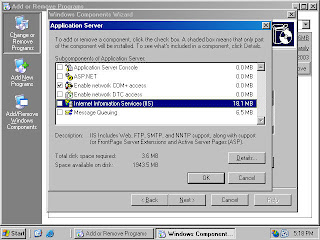
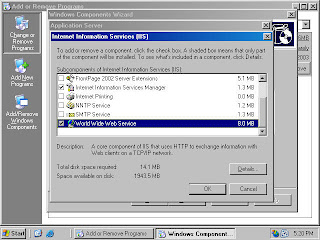
For example
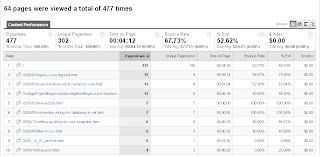
64 pages were viewed a total of 477 visitors (i.e. Visit only a single page of a site).
(Single page visit / total page visits) * 100 = Bounce Rate
(64 / 477) * 100 = 67.73%
Importance of reducing bounce rate:
- Visitors Time on the Page to be increased (i.e. visitors will stay longer in the site) and
- Conversion rates will improve.
You can determine it by using Google Analytics tool
- Go to Content -> Top Content.
- Now you can view the Bounce Rate column (it shows bounce rate for particular page).
To reduce bounce rate:
No hard and fast rule to reduce bounce rate.
- Increase the overall feel of that particular page.
- Look at the navigational structure.
- Take care when you assign a heading to the page or article and it should be more appropriate to the content because visitors are reading your headline and calling it off.
- Show the high bounce pages to your friends/colleagues. Ask them what they find annoying. Listen to them carefully - implement it and see if there is a change in bounce rate.